Friday Hacker Blogging: How To Watch Star Wars In Linux Terminal (and update on Canon hacker attack)
For the Friday Hacker blogging series here is something that’s as fun as it is useless, but it will appeal to all those hardcore Star Wars fans.
You can watch Star Wars in Linux terminal (not just Linux, every *nix flavor will likely work). We are not talking about a digitally remastered version here, no high res graphics or else. In fact there are no graphics in a modern meaning. All you have to do is to enter the following command in your terminal:
telnet towel.blinkenlights.nl
You can stop the “movie” with ctrl-j, and then type quite to exit.
Should you not have telnet on your system you can easily install it. For instance on Ubuntu or Debian:
sudo apt install telnetHere are two screenshots.
Ready for Star Wars in Linux terminal?
Canon Ransomware Attack
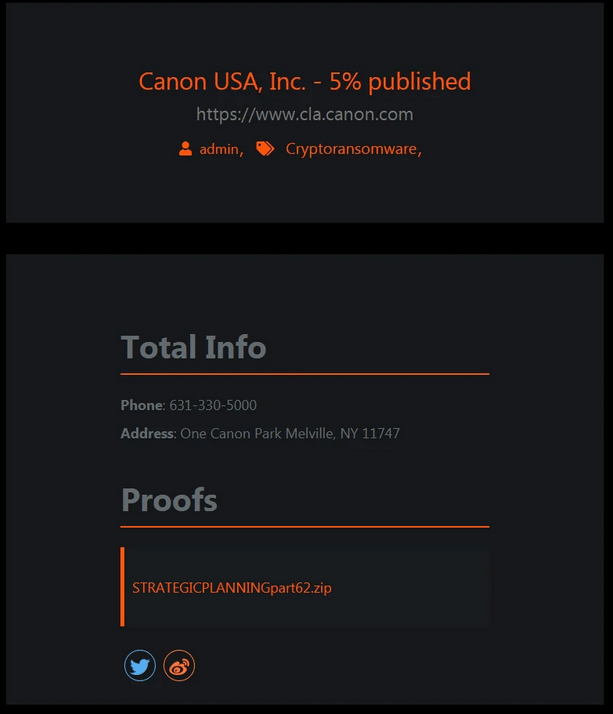
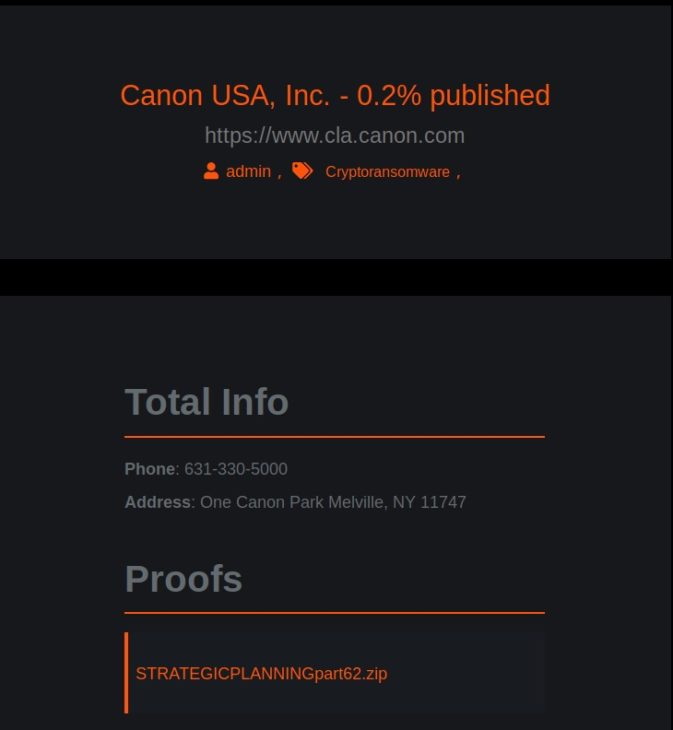
Here is also an update on the ransomware attack against Canon. See here for an update or if you don’t know what a ransomware attack is. The Maze ransomware gang updated their leak site and now it states that “0.2%” of Canon data was published. Previously it was 5%. We do not know yet what exactly that means. Also, we obtained a copy of the leaked Canon data and can confirm it does not contain sensible sensitive or otherwise critical information.
You can use the Friday Hacker Blogging post to discuss whatever topic you want. Please be respectful and polite.