There might be some rare cases forcing you to rollback to an older firmware version…
Friday Hacker Blogging: Get Doom Running On a Canon PIXMA Printer
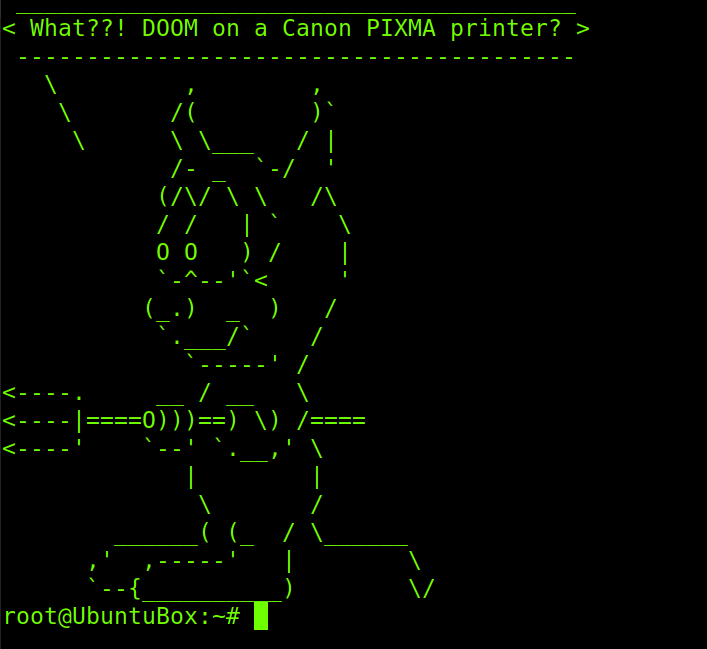
Back in 2014 security researcher found a vulnerability in Canon PIXMA printers. They demonstrated the vulnerability by installing the 1990’s game Doom on the printer.
Canon wireless Pixma printers can be accessed through a web page, for instance to see printer information like ink levels or to update the firmware.
Says the hacker at Context (emphasis added):
This interface does not require user authentication allowing anyone to connect to the interface. At first glance the functionality seems to be relatively benign, you could print out hundreds of test pages and use up all the ink and paper, so what? The issue is with the firmware update process. While you can trigger a firmware update you can also change the web proxy settings and the DNS server. If you can change these then you can redirect where the printer goes to check for a new firmware. So what protection does Canon use to prevent a malicious person from providing a malicious firmware? In a nutshell – nothing, there is no signing (the correct way to do it) but it does have very weak encryption. I will go into the nuts and bolts of how I broke that later in this blog post. So we can therefore create our own custom firmware and update anyone’s printer with a Trojan image which spies on the documents being printed or is used as a gateway into their network. For demonstration purposes I decided to get Doom running on the printer (Doom as in the classic 90s computer game).
And Doom it was:
Canon acknowledged the issue and provided the following statement regarding this issue:
“We thank Context for bringing this issue to our attention; we take any potential security vulnerability very seriously. At Canon we work hard at securing all of our products, however with diverse and ever-changing security threats we welcome input from others to ensure our customers are as well protected as possible.
We intend to provide a fix as quickly as is feasible. All PIXMA products launching from now onwards will have a username/password added to the PIXMA web interface, and models launched from the second half of 2013 onwards will also receive this update, models launched prior to this time are unaffected. This action will resolve the issue uncovered by Context.”
It is a good practice to never connect a printer to the Internet.
If you want to dive deeper into the hacking and learn how Canon’s encryption was broken read the article at Context. This post can be used to discuss about whatever topic you want.